Ultimate DLP for Microsoft 365 & Google Workspace
Full control on data flow across every tenant. Prevent data exfiltration, insider threats, and accidental sharing with AI-powered protection.
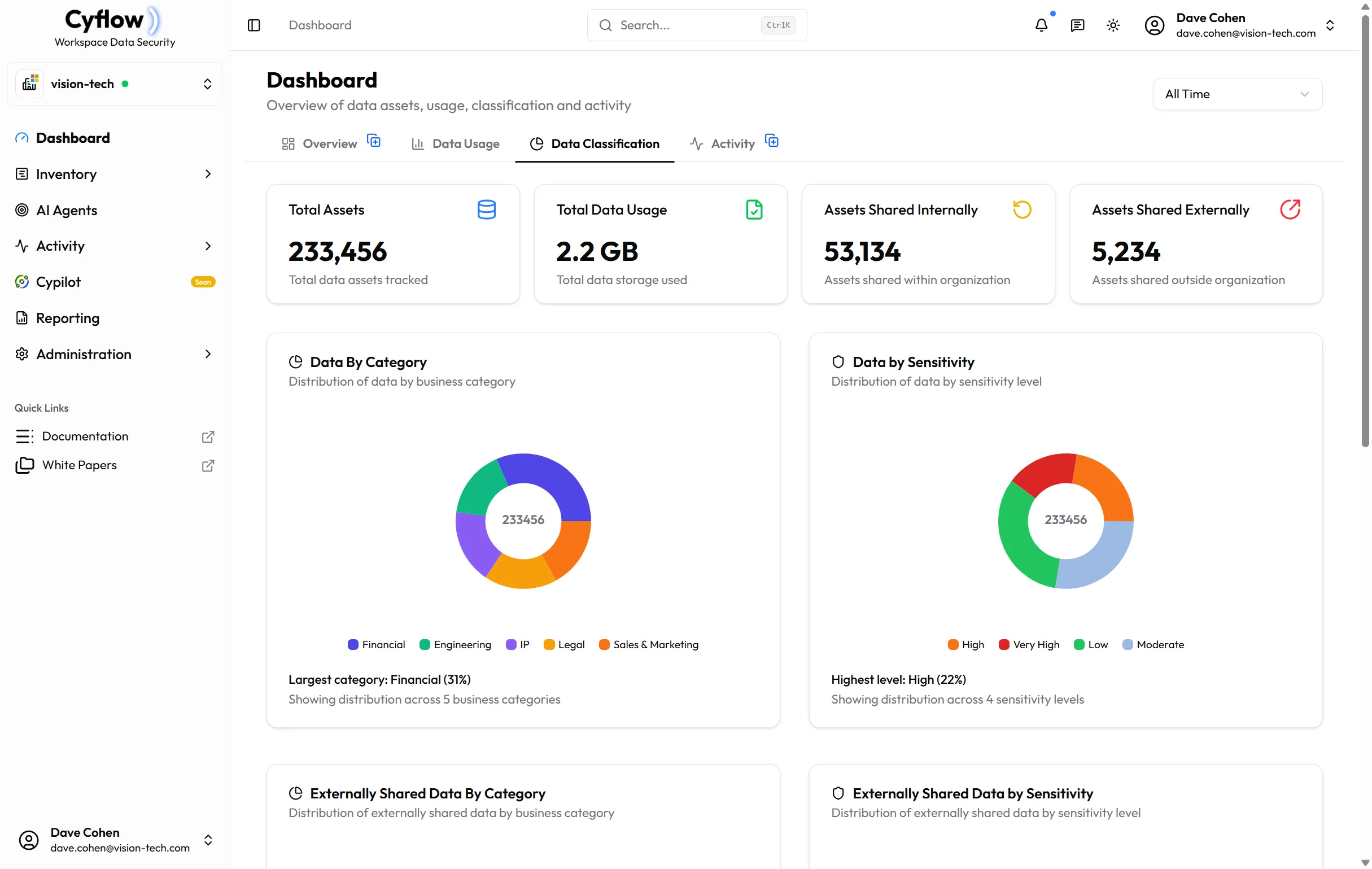
Classify and Protect Sensitive Data
Complete access control over sensitive data
Control who can access your sensitive data and when. Identify overly permissive shares, manage external access, and enforce least-privilege policies automatically across your entire workspace.
AI-powered classification and autonomous remediation
Our AI automatically classifies sensitive data including PII, PHI, and intellectual property. Configure your policies once and let our AI agents handle the rest with 24/7 automated remediation.
Real-time monitoring and compliance reporting
Get instant alerts on policy violations and suspicious activities. Generate comprehensive compliance reports for GDPR, HIPAA, and SOC 2 with a single click. Stay audit-ready at all times.
Complete Data Protection
Sensitivity Classification
Files graded by sensitivity level across GDPR, HIPAA, SOC2, PCI, and ISO27001 compliance schemes.
External Share Detection
Find files shared externally, via public links, or to personal email addresses outside your organization.
One-Click Revocation
Remove risky permissions instantly. Bulk actions let you clean up hundreds of shares at once.
AI Agent Remediation
Configure agents to automatically revoke dangerous shares 24/7 across all client tenants.
Simple as One, Two, Three
Onboarding
Familiar and Super Fast
Sign in with your Microsoft 365 or Google Workspace account. No complex setup required.
Agents Configuration
Predefined and Custom
Choose from our library of pre-built agents or create custom ones tailored to your needs.
Sit Back and Relax
Continuous Remediation
Our AI agents continuously monitor and automatically remediate security issues. Get regular reports.
