AI-Powered Data Security for
Autonomous workspace protection that monitors, detects, and automatically remediates data security risks across Microsoft 365 and Google Workspace — before they become breaches.
Works seamlessly with your workspace
See Your Security Posture at a Glance
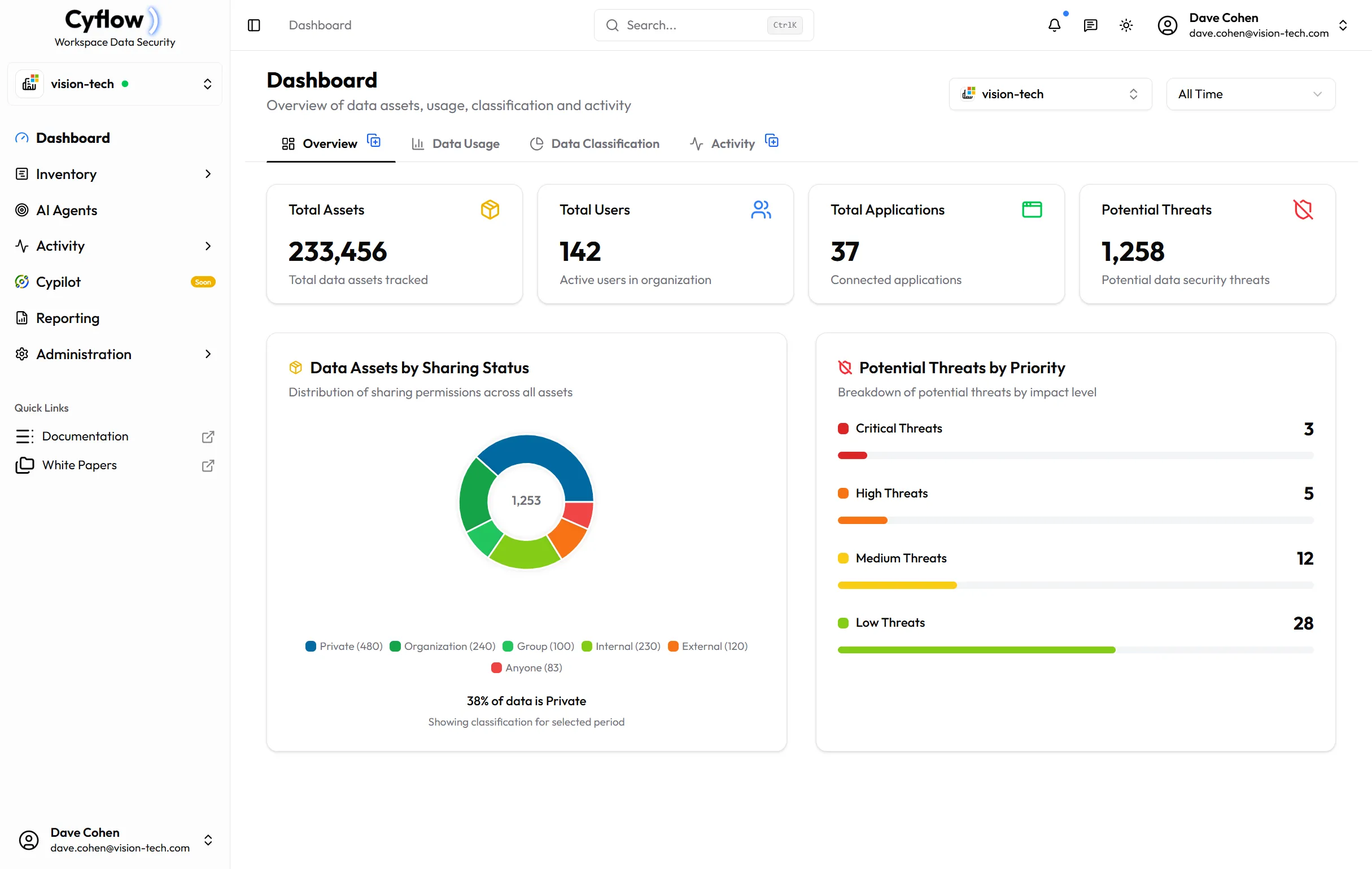
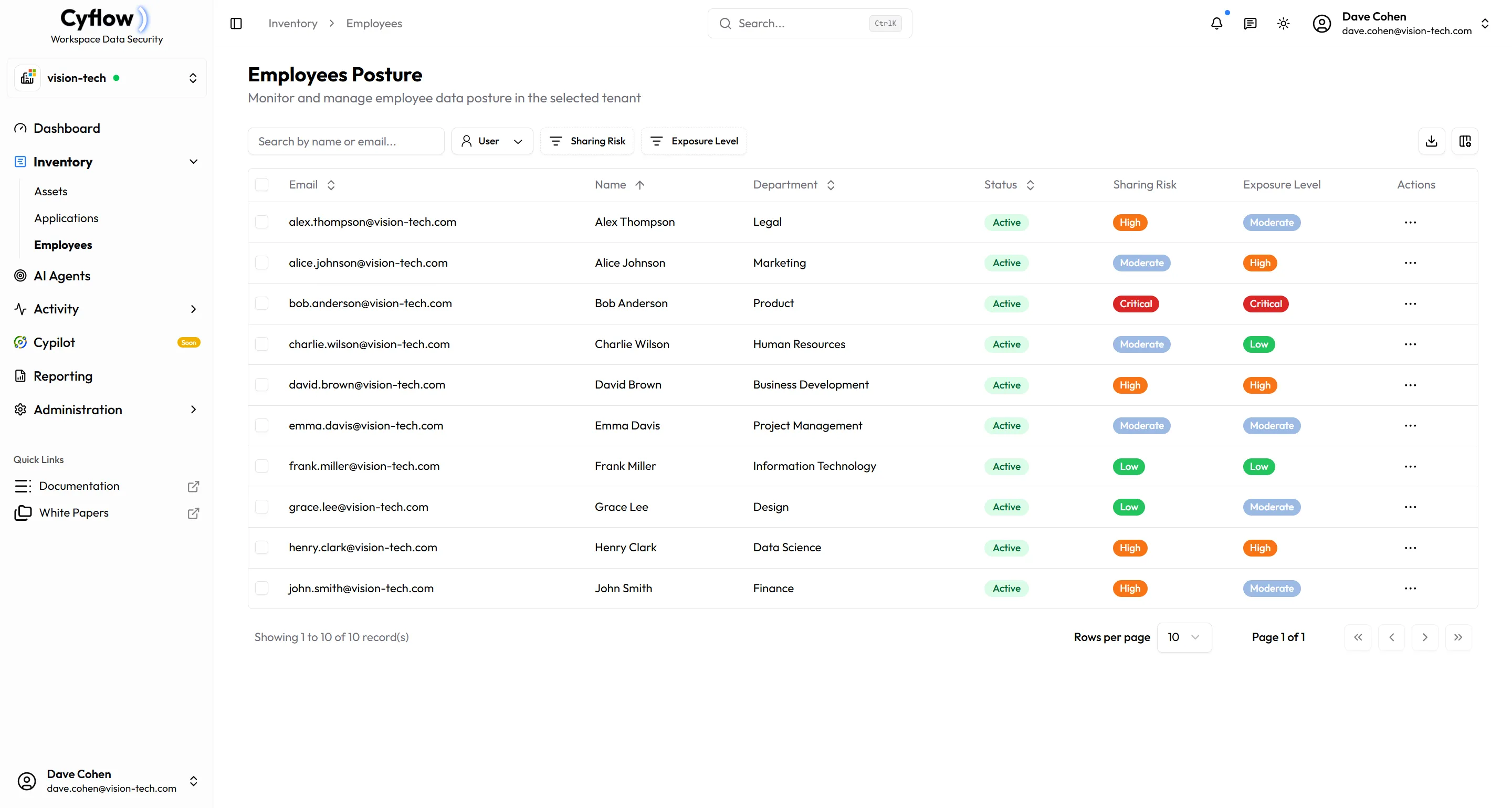
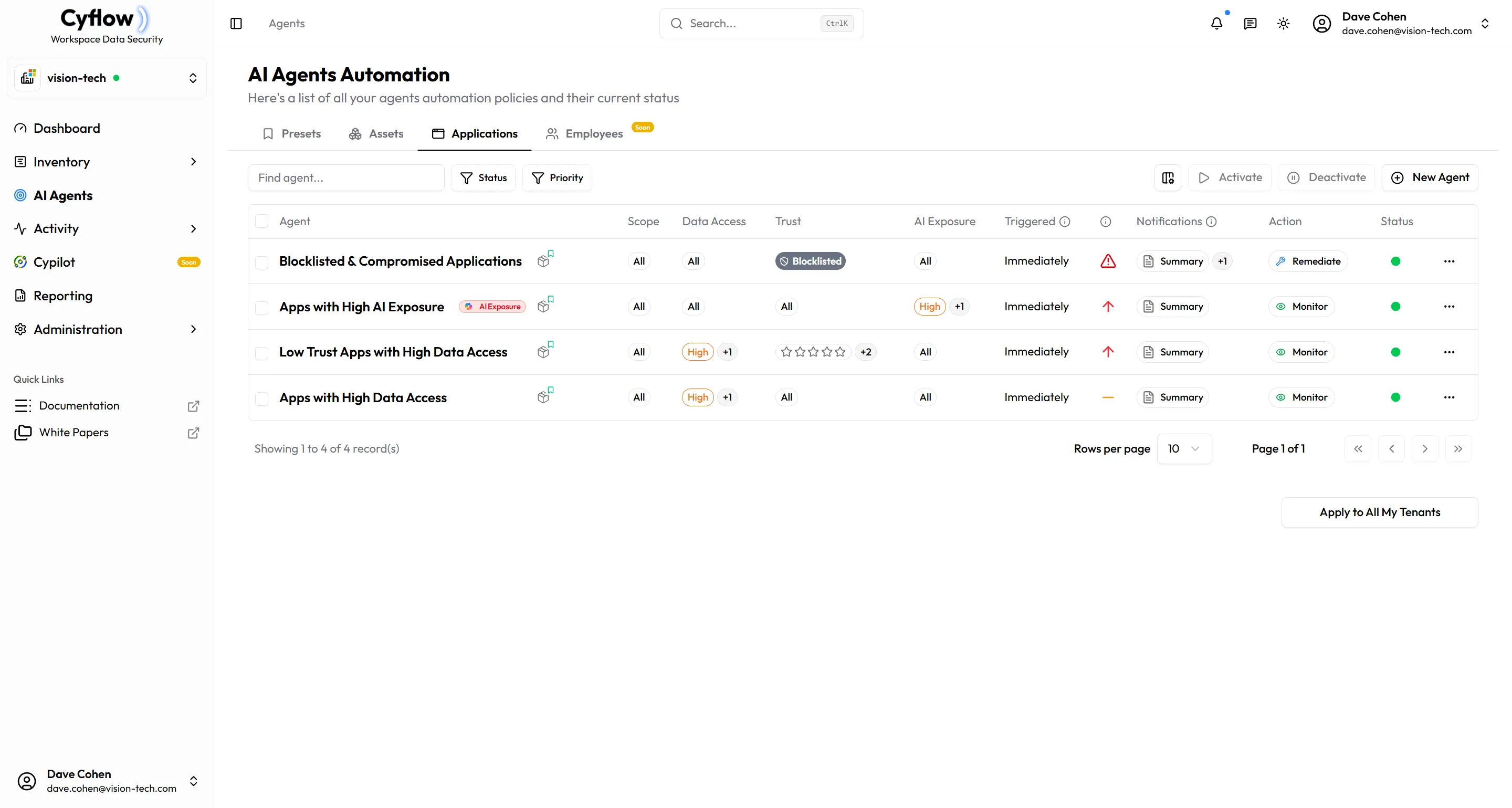
Finally, Data Protection That Works
Access Management
Control overly permissive shares, former employees, and private email access
DLP
Prevent insider threats, data exfiltration, and accidental sharing
AI Exposure
Monitor exposure via AI assistants and SaaS applications
Inventory Visibility
Complete visibility into all your data assets
AI Classification
Automatically classify and categorize sensitive data
Collaboration Security
Secure external sharing and collaboration
PII & PHI
Detect and protect personally identifiable and health information
Blazing Fast
30-second onboarding with instant results
Set and Forget
Autonomous protection that works while you sleep
Built-in AI Agents
Pre-configured agents for common security scenarios
Custom AI Agents
Create your own agents tailored to your needs
Usage Reports
Comprehensive reports on data usage and access patterns
Simple as One, Two, Three
Onboarding
Familiar and Super Fast
Sign in with your Microsoft 365 or Google Workspace account. No complex setup required.
Agents Configuration
Predefined and Custom
Choose from our library of pre-built agents or create custom ones tailored to your needs.
Sit Back and Relax
Continuous Remediation
Our AI agents continuously monitor and automatically remediate security issues. Get regular reports.
Protect Your Workspace Today
Start your free 14-day trial. No credit card required.
