360° Visibility Into Every User's Data Security
See who's exposing sensitive data across client organizations, detect insider threats before they escalate, and ensure MFA compliance. Real-time risk scoring powered by behavioral analytics.
Monitor Every User's Risk Profile
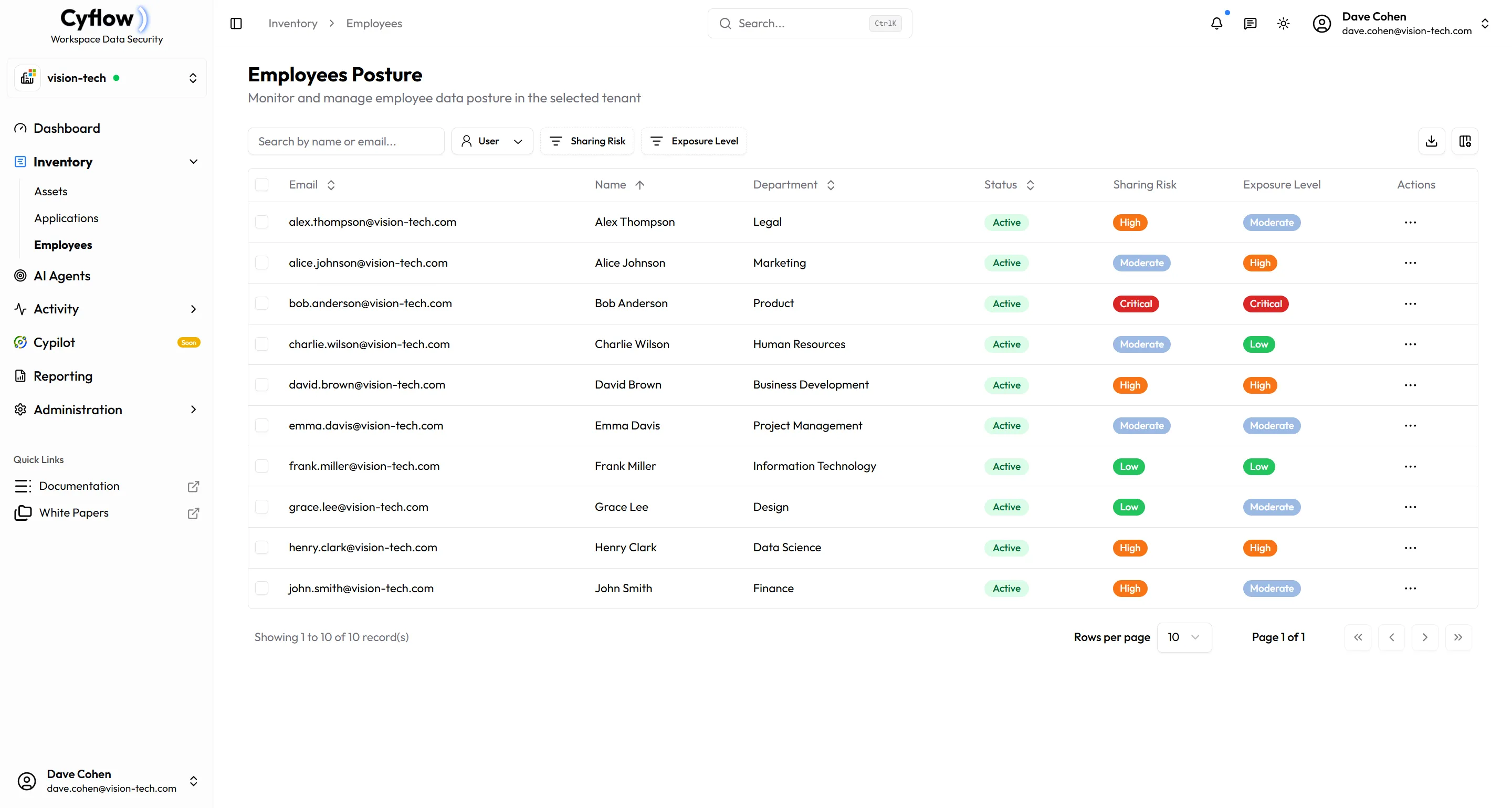
Dynamic risk scoring for every user
Each employee receives a real-time risk score based on their data sharing behavior, external access patterns, and sensitive file exposure. Track external shares, internal shares, and sensitive data movement with granular visibility. Instantly identify who poses the highest risk to your organization.
Detect insider threats before they strike
Our behavioral analytics engine learns normal patterns and flags anomalies in real-time. Whether it's unusual download activity, mass external sharing, or access from suspicious locations—you'll know immediately. Monitor departing employees, track privilege escalation, and investigate suspicious activity with complete audit trails.
Enforce MFA and verify identity across your workforce
Get complete visibility into MFA adoption across your organization. Identify users without multi-factor authentication, track enrollment status, and automate enforcement policies. Combine with AI-powered identity verification to ensure only authorized users access your sensitive data.
Complete User Visibility
User Risk Scoring
Each employee gets a risk score based on external shares, internal shares, and sensitive data exposure.
Data Exposure Metrics
Track total files, size, and sharing patterns per user. Identify who poses the highest risk.
Security Score Dashboard
Aggregate security and AI resilience scores calculated from sensitive data sharing patterns.
Activity Monitoring
Track file activity, permission changes, and sharing events with complete audit trails.
Simple as One, Two, Three
Onboarding
Familiar and Super Fast
Sign in with your Microsoft 365 or Google Workspace account. No complex setup required.
Agents Configuration
Predefined and Custom
Choose from our library of pre-built agents or create custom ones tailored to your needs.
Sit Back and Relax
Continuous Remediation
Our AI agents continuously monitor and automatically remediate security issues. Get regular reports.
Know Your Users' True Risk
Start monitoring user security posture in minutes.
