TL;DR: The next "breach" won't be a hacker in a hoodie. It'll be a spreadsheet in an email. The only winning move is shrinking the blast radius.
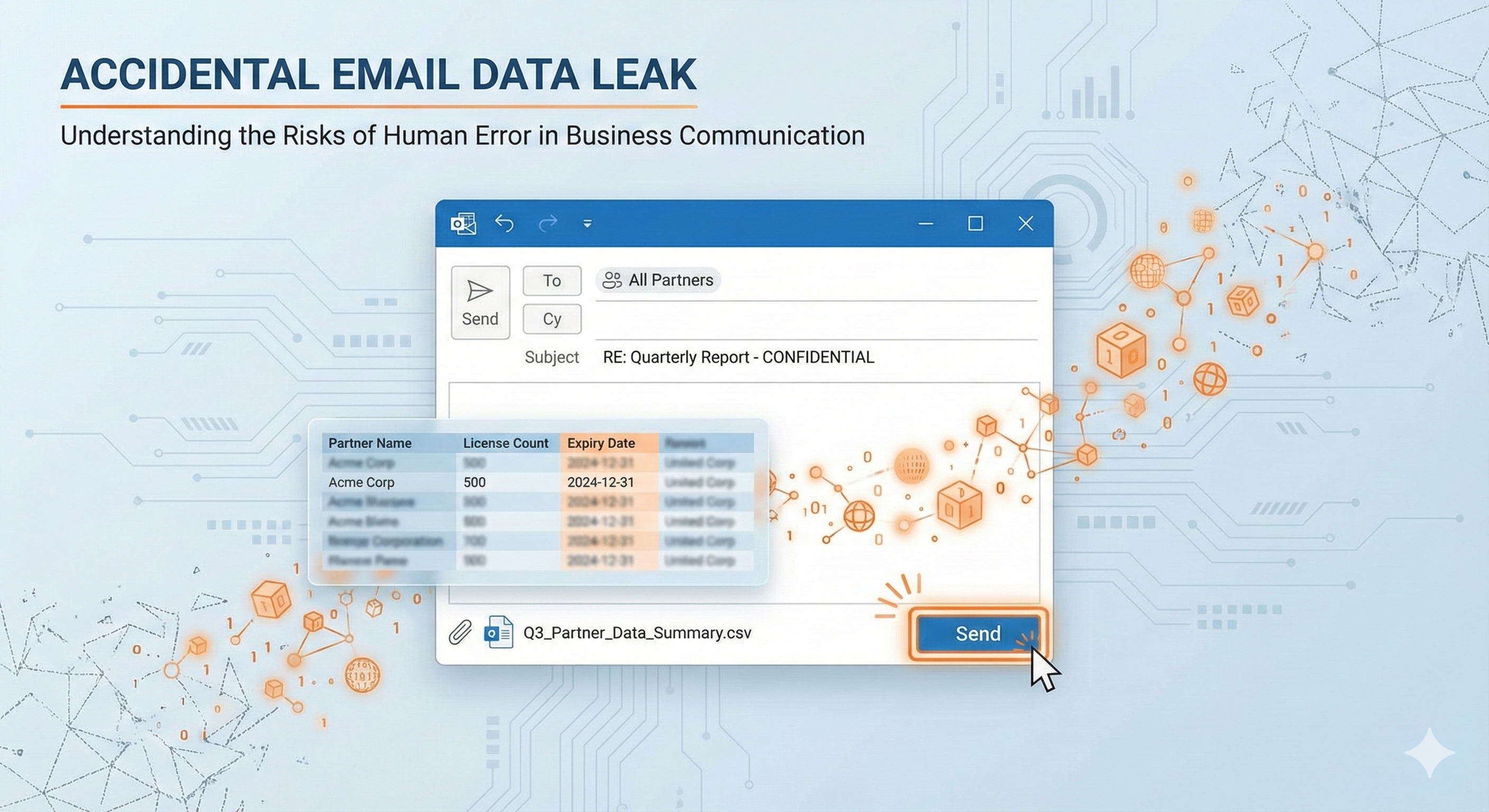
The Pax8 Incident: Not a Hack—an "Oops"
Last week, Pax8 confirmed an employee accidentally sent a CSV attachment to fewer than 40 recipients—but the file contained sensitive internal business data tied to roughly 1,800 partners. Customer names, licensing SKUs, counts, renewal dates, commercial details—the kind of information that turns into a targeting list the moment it escapes the room.
And yes: threat actors reportedly started asking for it.
The Uncomfortable Truth: Mistakes Are Inevitable
We love "zero trust." We buy "AI security." We run tabletop exercises. Then someone clicks Send.
Humans mis-deliver. Humans overshare. Humans attach the wrong file. Humans forget a permission was set to "anyone with the link." It's not incompetence—it's math. High-speed collaboration + constant context switching + a million tiny decisions = eventually, something slips.
So if your security strategy is "prevent every mistake," you're building on vibes.
The Goal Isn't Perfection. It's a Smaller Blast.
When the inevitable happens, three things matter:
- Guardrails: make it hard to share the wrong way.
- Visibility: know what was shared, with whom, and whether it's sensitive.
- Fast remediation: removing access should happen automatically—or at least with one click—not a project plan.
That's how you turn "breach" into "near-miss."
This Is Exactly Why We Started Cyflow
Cyflow is built around a simple belief: data is the target. Everyone is after it—criminals, competitors, and increasingly, automated systems that scale faster than humans can keep up.
In this Pax8-style scenario, Cyflow's Secure Share approach changes the outcome:
- All sharing is routed through the company's OneDrive (not attachments, not personal accounts, not random storage, not "wherever the file happened to be").
- Cyflow continuously tracks what's being shared and flags risky exposure—like "this sensitive dataset is effectively public."
- Remediation is immediate: revoke access, close the link, cut the blast radius—fast.
You can't always stop the first mistake. But you can stop it from becoming a headline.
If You Assume a Breach Will Happen, You Can Actually Win
The organizations that do best aren't the ones who promise "never." They're the ones who design for "when."
If you want to see how Cyflow reduces blast radius in Microsoft 365 sharing, take a look at our Microsoft 365 coverage and built-in agents—or reach out and we'll walk through it live.
Ready to Shrink Your Blast Radius?
Deploy Cyflow in 30 seconds and detect oversharing before it becomes a breach.
