Complete Visibility and Control Over File Access
Know exactly who has access to every file across your client base. Identify oversharing, manage external access, and enforce least-privilege policies automatically.
Complete Visibility Into Every Permission
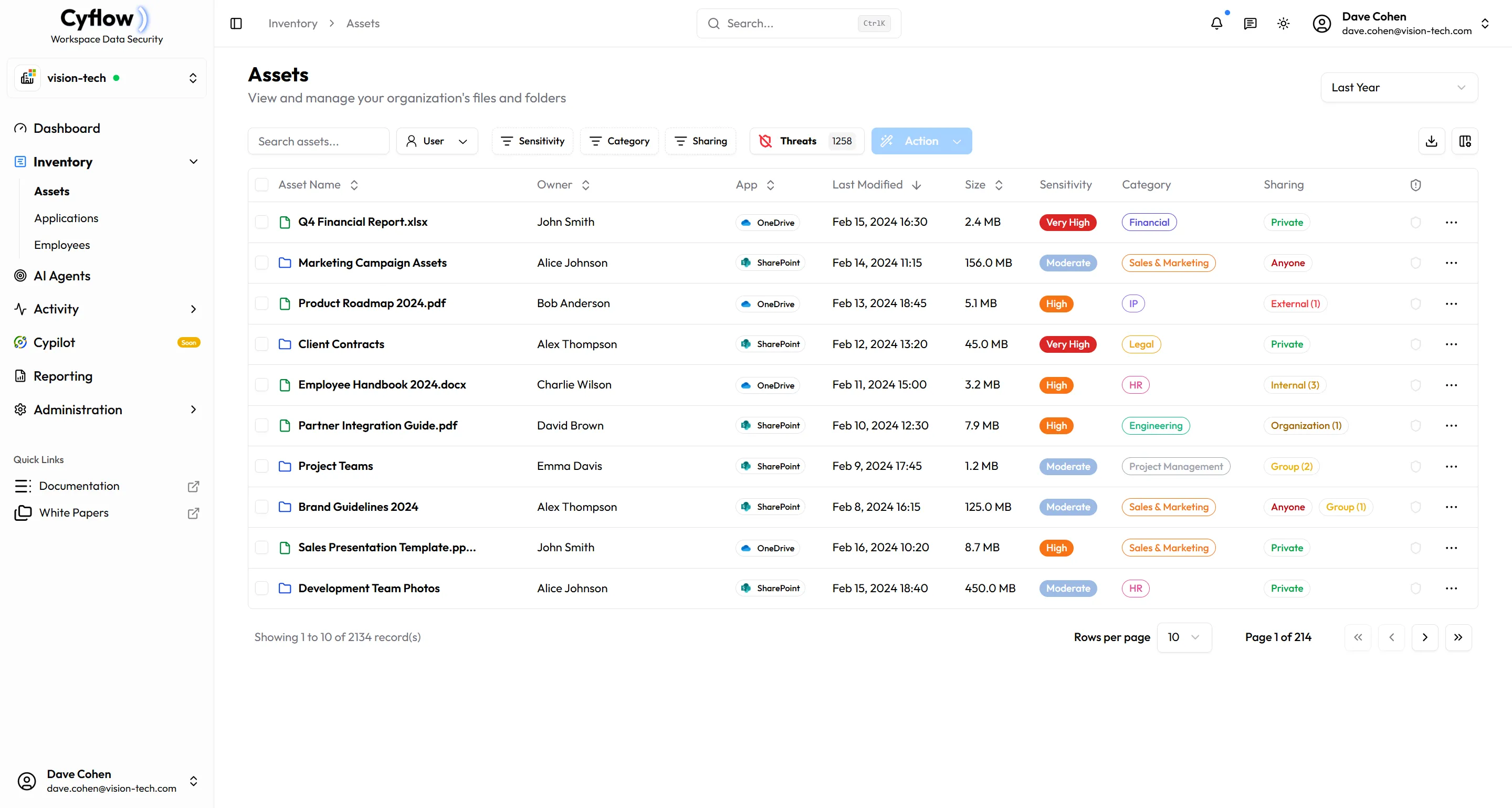
See exactly who has access to every file
Gain complete visibility into all permission types across your workspace. Track internal users, external collaborators, group memberships, domain-wide access, and public links. Know who granted each permission and when, with full audit trails for compliance.
Detect and remediate overly permissive shares
Automatically identify risky sharing patterns like 'Anyone with Link' public shares, files sent to personal email addresses, and overly broad domain-wide permissions. Get instant alerts when sensitive data is exposed beyond its intended audience.
Take action with one click or let AI handle it
Revoke permissions instantly with a single click, or configure AI agents to automatically remediate risky shares based on your policies. Bulk actions let you clean up thousands of overshared files at once, while smart automation handles the rest 24/7.
Access Management Features
External Sharing Detection
Identify files shared outside your organization to contractors, partners, or unknown recipients
Public Link Detection
Find dangerous 'Anyone with Link' shares that expose sensitive data to the entire internet
Group & Domain Access
Control organization-wide and group permissions to prevent unnecessary broad access
One-Click Revocation
Remove access instantly across any tenant. No complex workflows required.
AI Threat Detection
AI agents continuously monitor for risky sharing patterns and alert you in real-time
Least Privilege Enforcement
Automatically enforce minimum necessary access policies across your workspace
Former Employee Access
Detect and revoke access retained by departed employees to prevent data leakage
Personal Email Detection
Find sensitive data shared to personal email accounts outside corporate control
Simple as One, Two, Three
Onboarding
Familiar and Super Fast
Sign in with your Microsoft 365 or Google Workspace account. No complex setup required.
Agents Configuration
Predefined and Custom
Choose from our library of pre-built agents or create custom ones tailored to your needs.
Sit Back and Relax
Continuous Remediation
Our AI agents continuously monitor and automatically remediate security issues. Get regular reports.
Take Control of Your Data Access
Start managing permissions in minutes with a free 14-day trial.
